Microsoft_authentication_package_v1_0

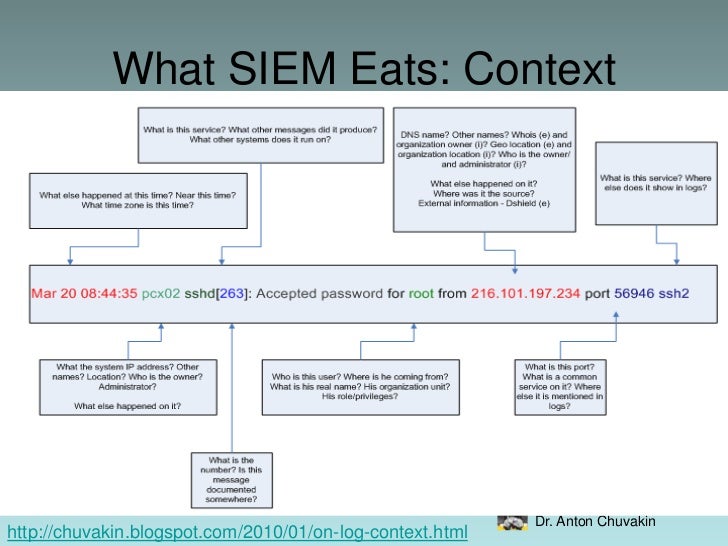
Today, I had the lovely experience in trying to troubleshoot why a users account was locking out of the domain every 30 seconds. Inside of event viewer, I could see the account failing to login, but I had the most generic, useless, log to help track down what was going on.
The computer attempted to validate the credentials for an account.
Authentication Package: MICROSOFT_AUTHENTICATION_PACKAGE_V1_0
Logon Account: username
Source Workstation:
Error Code: 0xc000006a
Scrolling through my logs, the only other thing I was was the error code switching from from a 0xc000006a to a 0xc000234. Even though this is beyond the scope of this document, here are what those codes mean:
Also MICROSOFTAUTHENTICATIONPACKAGEV10 is not a user login ID, is an Authentication Package. It should appear against 'Authentication Package:', not 'Logon attempt by'. Your PC is most likely infected, but not much info on ADVAPI yet. Authentication Package: This is always 'MICROSOFTAUTHENTICATIONPACKAGEV10'. Logon Account: The name of the account that attempted a logon. The account can either be a user account, a computer account, or a well-known security principal (e.g. Everyone or Local System). Source Workstation: The name of the computer the logon attempt originated. Welcome to this November Patch Monday Bulletin. This month there are updates for Adobe, Apple, Google, and Mozilla. The biggest issue this month is Chrome with 3 vulnerabilities that were actively attacked in the wild. A client application calling the remote object (running as a windows user logged on to the domain/Actiev directory): MICROSOFTAUTHENTICATIONPACKAGEV10; A client application calling the remote object, running as a local Windows user (no AD user): NTLM.
Autocom delphi 2016 keygen free download. This event id has been occurring frequently on the domain controller and the details as follows: Authentication package: MICROSOFTAUTHENTICATIONPACKAGEv10 l.
0xc000006a – An invalid attempt to login has been made by the following user.
0xc0000234 – The user account has been automatically locked because too many invalid logon attempts or password change attempts have been requested.
Anyways, after scrolling through event viewer on my domain controllers, trying LockoutStatus.exe, and asking the user to power off their mobile devices, workstations, etc, in a desperate act, the error still peristed. Finally I came across the holy grail of Microsoft articles: http://support.microsoft.com/kb/109626/en-us
Solution: We had to put the domain controller in verbose logging for the netlogon service to actually find out where the logon attempt was coming from.
First, open up command prompt as an administrator and execute the following command:
nltest /dbflag:0x2080ffff
Once done, execute the following command to turn off the debugging:
nltest /dbflag:0x0
Microsoft_authentication_package_v1_0 Audit Failure 4625
This logs every transaction made to the file: %windir%debugnetlogon.log (note, you need to run notepad as an administrator to read this file).
Microsoft_authentication_package_v1_0
Inside of there, find the logon attempt made by the user and it should list the workstation it came from. In this case, the logon attempt was coming from our NPS server, which then was coming from an old laptop he had logged into and left alone for a few months.
